Introduction
Blockchain technology has revolutionized various industries by offering a secure and transparent system. At its core lie cryptographic hash functions, ensuring the integrity, security, and immutability of blockchain networks. We explore the significance of this hash functions in the blockchain ecosystem and their contributions to the trustworthiness of this innovative technology.
What are Cryptographic Hash Functions?
Cryptographic hash functions are mathematical algorithms that produce fixed-size hash values from input messages. They are designed to be fast and efficient, making them ideal for use in blockchain systems.
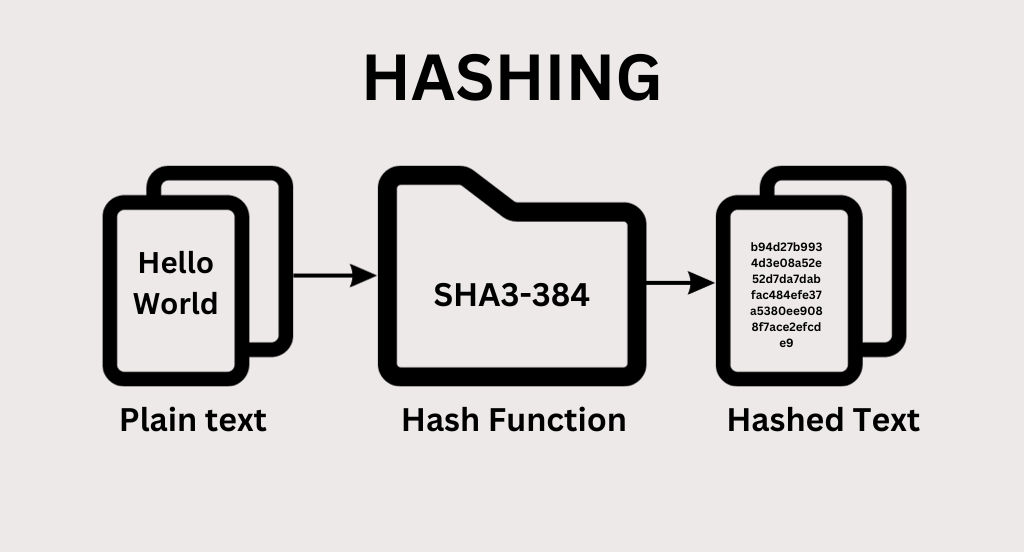
Properties of Cryptographic Hash Functions
- Deterministic:
- Cryptographic hash functions ensure consistency and predictability in blockchain networks by producing the same output for the same input.
- Quick Computation:
- These functions provide fast computation speeds, enabling efficient processing of transactions and data within a blockchain.
- Pre-image Resistance:
- Ensuring data privacy and security, it is computationally infeasible to determine the original input message from its hash value.
- Collision Resistance:
- This hash functions minimize the likelihood of different inputs producing the same hash output, making it difficult for attackers to tamper with data integrity.
The Role of Cryptographic Hash Functions in Blockchain
- Data Integrity:
- Each block in a blockchain contains a unique hash value representing the data within that block. Any changes to the block result in a different hash value, alerting the network to tampering attempts and ensuring data integrity.
- Block Verification:
- Verifying the integrity of previous blocks when new blocks are added, this functions include the hash of the previous block in the current one. This detects alterations, maintaining the chain’s integrity.
- Digital Signatures:
- Playing a vital role in generating and verifying digital signatures, this hash functions create a digital signature by applying a hash function to the message and encrypting it with the sender’s private key. The recipient verifies the signature using the sender’s public key and compares the hash of the received message with the decrypted signature, ensuring message authenticity and integrity.
- Proof-of-Work (PoW):
- An essential component of PoW algorithms securing decentralized blockchain networks like Bitcoin, this hash functions are used by miners competing to solve complex mathematical puzzles. This process requires significant computational power, ensuring no single entity can easily manipulate the blockchain.
Emerging Trends in Blockchain Technology
Stay updated with the latest trends and advancements in the blockchain space. Explore emerging trends in blockchain technology for insights into the future of this transformative technology.
Conclusion
This hash functions are fundamental to blockchain technology, providing security and integrity to decentralized systems. Their deterministic nature, quick computation, and resistance to pre-image and collision attacks make them invaluable in various aspects of blockchain implementation. As blockchain continues to advance and find applications across industries, understanding the role of this hash functions becomes increasingly important for developers, users, and stakeholders

